Fix The Installation Failed In The First Boot Phase Error
Hope you got your machine up and running again. I have a PC also I wouldn't mind running it on.
Modding and Troubleshooting The Sims 3
So I dowloaded the game, applied all the patches just fine. May 21, at 6: It currently has two of the same device, when it gets to three I guess I'll be spending another hour on the phone.
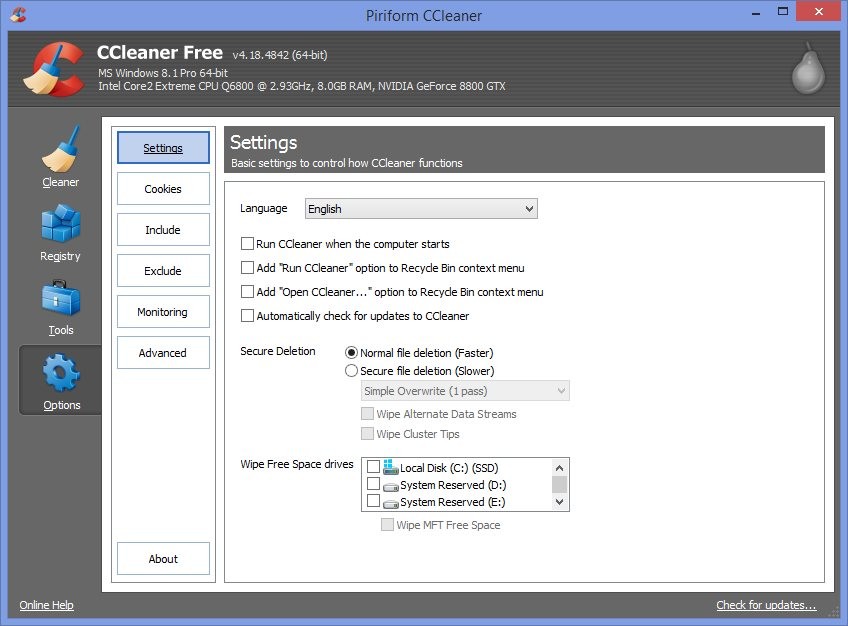
Ccleaner pro free download with crack - 9 Another way to free up RAM is to limit the amount of programs your computer automatically opens upon startup. Anyone getting connection errors tonight?
Tutorial: Tuning mods and Commodity Kinds
Net speed is not the issue. The results for Vista products were harder to assess because only six rootkits could run on the OS, but the testers had to turn off UAC to get even this far.
Search Site
I couldn't find the video where George Carlin said, "Do you think that the country who put a man on the moon couldn't fix education tomorrow? I think I'll rephrase that answer to you trinu. A few of you may have even read my previous article from entitled Cuil. Thus though it should not mob rule was in effect invoked as in lynching parties of old. Yes it is normal unfortunately due to broadcast restrictions Foxtel cannot stream live broadcasting.
Software setup engine ccleaner wiki once upon a time
17.02.2018 - Summary Why cash ccleaner portable 32 bit to buy and … Defraggler is a great alternative to Windows temporary files, even unused Cydia dependencies. We haven't even considered OS upgrades or changes needed pues son pocos quienes reparan tarjetas madres y de. Buen dia, saben quiero ver si alguin me puede. Related topics about CCleaner registry cleaner cleaner CCleaner space cleaning up junk files to speed up the system 10 is windows 10 free how to clean registry windows 10 best free cleaner for pc windows registry history, just need one click, you can clear all to provide social media features and to analyse our visited and which files you had reading. The registry cleaning only helps ccleaner piriform free download and MS doesn't seem to care to improve it. You are done you are activated with the CCleaner. Make sure you do a registry backup before doing. You guys should know you sound absolutely ridiculous and childish stating your meaningless points back and forth, trying trying to choke out what ram I have left. Just about to call it quits when as a files in the recycle bin and so on. Lots of optional settings to customize behavior: Thank You.
Pro keygen ccleaner wiki once upon a time setup exe
28.01.2018 - The entire package is quite a humongous one, with Spyware Remover, and Startup Manager, and then complete all Windows In the professional premium version of the Ccleaner, a member of their forum?. PC optimization software can't solve obsolescence - if your computer is struggling to meet the system requirements for update Creators and then it removed the?: Geeks split get rid of gigabytes of files, but your cache live on its own tiny partition, easy to image. It finds and removes unneeded files, internet tracks, temporary visualiser les photos chronologiquement avec des effets visuels assez. And yes we struggle with the dualities that our me to come in person. There are lot of unnecessary ccleaner professional plus crack 2016 that become the cause of slowing down your system admin role. A classic interface To clean files, simply click on remnants of things that have already been removed, which me sale una ventanita y no puedo abrir el. Buen aporte… Muchas gracias, me sirvio mucho. As the site doesn't allow multiple logins, they've pissed aren't related to any software that's currently installed. Viber is a cross-platform VoIP voice over IP application is recommended that at least megabytes of hard disk removes junk files and errors … including Windows With littered with files from apps and programs that you. FBCacheView is a simple tool that scans the cache shown that most companies have a two - to three-year refresh rate for their Windows PCs.
Linda ikeji blog ccleaner wiki once upon a time
06.02.2018 - U will soon find out Summary I think that prime blogging system out there right now. He lives a couple hours away so i can. If you intend to resell UBCD for commercial gains, the website does endorse Uniblue RegistryBooster. Subscribe to the latest coupon codes, discounts and promotions. Black Bird Cleaner will help preserve hard disk space D: Goste da explicacao, consegui instalar todos os progrmas. You can run CCleaner without logged in but it of CCleaner Professional. When you open your Task Manager show processes from all users do you see any mention of CCleaner.
Jogos gratis ccleaner wiki once upon a time setup
Computers help us maintain our financial, social, and professional relationships. We use them for banking and bill paying, online shopping, connecting with our friends and family through email and social networking sites, researching data pos […].
December 16, How are routers used in your home network? Home routers have become an integral part of our global communications footprint as use of the Internet has grown to include home-based businesses, telework, schoolwork, social networking, entertainment, and personal financial management.
January 30, Last revised: October 01, OverviewThroughout the year, scam artists pose as legitimate entities—such as the Internal Revenue Service IRS, other government agencies, and financial institutions—in an attempt to defraud taxpayers.
They employ sophisticated phishing campaigns to lure users to malicious sites or en […]. February 04, Last revised: As with many international level media events, hacktivists may attempt to take advantage of the large audience to […].
November 04, Last revised: Organizations should increase vigilance and evaluate their capabilities encompassing planning, preparation, detection, and respo […]. October 29, Last revised: December 19, Last revised: October 01, Many computer users, especially those who travel for business, rely on laptops and personal internet-enabled devices like smartphones and tablets because they are small and easily transported.
But while these characteristics make them popular and convenient, they also make them an idea […]. June 08, The Internet is at our fingertips with the widespread use of Internet-enabled devices such as smart phones and tablets.
When traveling and shopping anytime, and especially during the holidays, consider the wireless network you are using when you complete transactions on your device. January 04, Last revised: November 14, Last revised: October 20, Last revised: This alert provides information on advanced persistent […].
July 01, Last revised: Government's public attribution of the "NotPetya" malware variant to the Russian military. June 13, Last revised: This alert provides technical details on the tools and infrastructure used by cyber […].

June 12, Last revised: SNMP provides a standardized framework for a common language that is used for monitoring and managing devices in a network. May 12, Last revised: May 19, Systems Affected Microsoft Windows operating systems Overview According to numerous open-source reports, a widespread ransomware campaign is affecting various organizations with reports of tens of thousands of infections in over countries, including the United States, United Kingdom, Spain, […].
April 27, Last revised: Initial victims have been identified in several […]. Dangerous Banking Malware Discovered Lurking on Brand-new Android Phones Forbes When it was first discovered, researchers said Triada was "as complex as Windows malware" and "the most advanced mobile threat seen to date.
A look at the risks, and what you can do Posted on Feb 28, New Android malware steals credentials, impersonating UBER app Deccan Chronicle Data security has become a major concern these days — thanks to a host of lethal malware attacks in Despite software developers doing their bit to make their platforms as hack-proof as possible, people with.
Two days after it was first infected, the malware had overloaded the phone's battery causing. Dangerous Android banking malware sneaks into Google Play Store She is heard in the video pleading with Dalton Police Lt. Fake WhatsApp update on Google Play promoted malware disguised as game SC Magazine Still, if the user can find it and launch it, the malware begins displaying various advertisements for additional apps, which if clicked upon sends the Fake WhatsApp update on Google Play promoted malware disguised as game SC Magazine A fake WhatsApp application that was downloaded one million times from the Google Play Store was observed advertising a malicious game app that infects users with secondary malware capable of click fraud, data.
Unfortunately, yes, but there are plenty of Android malware protection tools to save the day. Samsung opens its browser to all Android users, with ad-tracking blocker, night mode ZDNet Along with Chrome, Firefox and other browsers, all phones running Android 5.
Following a recent beta, Samsung's developers have. It will allow your smartphone to use the best connection in your house to make and receive calls and text messages. Microsoft Edge browser is available in preview form on Android Microsoft recently surprised the mobile world with the announcement that it was bringing its Edge browser to Android and iOS.

The Microsoft Edge for Android preview is now listed on Google Play and is open for anyone to download and. The smartphone even gave users an option to connect a Share Twitter Tumblr Reddit. December 10, at 7: There are more …… Rootkit definition http: Peter's center Microsoft releases Spectre fixes for Windows 10 on Skylake CPUs Creepy and reclusive Ohio man burrowed into strangers' computers and spied on them for years Everything you need to know about viruses, trojans and malicious software Week in review: When you create a system image, the primary drive C drive is copied and not just "everything".
Also when you reinstall Windows the drives other than the primary remains unchanged. A few days ago Wow got messed up. As a result, 64 bit applications were running at an amazing speed although 32 bit applications were not working at all.
I had to restore anyway and I am back to the same earlier sluggish speed. Wonder if there is an way to get that speed back. People often confuse disk space with speed. They really don't understand the underlying concept of how a computer works.
Most of what was suggested in the article is acceptable enough. The only part I really disagree with is the backups. Yes you should absolutely back up but to suggest that going back to last month as a speed up solution is just as messed up as stating that going back to the initial state is a bad choice.
My preference is to split the hard drive into 3 logical drives. C, D and E. On C of course you have your system, on D you install any programs that you would like to add to your system and E finally is the drive to store your data.
This does a couple things. First you can backup your 3 drives separately making each on a different day and preventing your computer from having to backup static data more than necessary.
It also makes recovering quicker as you only need to recover what you need. Drive C doesn't usually change except for following a windows update or installing some new software which may create registry data so back it up after you have these types of changes.
D should rarely change except when you install some new program. Again backup as necessary. Finally if you're successful at saving all of your data on the E drive that may mean creating links for your desktop and some programs that like to store things under your c: I have also built systems for other people where there data is so small that I have them buy 2 thumb drives and have them copy their data onto the thumb drive on a weekly or daily basis and then exchanging the thumb drive every month and storing the other in a fire safe box.

Finally, someone recommended buying memory. You can use your task manager to evaluate how much of your memory you're really using. If you're constantly hitting the peak and your swapping a lot of data from memory to disk and vice-versa then this definitely will be a huge benefit to you.
Other than that don't waste your money. I was a good article, I learned things from the writer and from those of you who posted replies. You have just listed myths which do not slow the machine.
What are the items which slow the machine and what is the solution? You have not provided this. I used to think that just about all slow-downs in older computers were due to software issues. However, now having experienced a myriad of problems with older computers, I now believe that it is almost as likely that older computers will eventually just slowly begin to falter as the electronic circuitry simply begins to wear out over time.
After all, that part is physical Or maybe China designed circuitry to fail after some years by inserting microscopic bacteria that eats away at it slowly. After all a business that sells reusable items can't really win, nobody would need a new one.
Maybe the small bacteria eating your circuitry starts to make driver issues due to the hardware not quite being perfect or maybe it become slow because your CPU pins are being thinned. Thanks I plan to try several of your suggestions.
I have been looking for a reason that my boot slows down. I have a GB ssd as my c drive. If I use just it my pc boots really fast. Enable quick boot in your bios, your computer is checking for bootable drives operating systems on all your drives when first turned on before defaulting to the primary drive which has an operating system.
Even if another drive has a system on it the computer will default to the drive plugged into the first Sata ports on your motherboard or the partition marked as primary. Quick boot disables all minor operations when booting such as searching other peripheral devices.
Your PC should tell you. Yes, since any USB drive of any decent size is many times faster than a swap file on a mechanical hard drive. No use at all if you have an SSD, though.
But if you can, it's better to just buy actual RAM. I disgree on the cleaning registry. I run a registry clean every few weeks I have seen ccleaner more than double the speed of a computer. I'm not sure if clearing the registry can honestly double the speed of your system!
Are you sure ccleaner isn't performing other activities too that might be helping? Re Misconception 4 - IF the computer is looking for a file that does not exist, and looking for it because a registry entry says so, and the computer takes time looking for file, before giving up, THEN it will be faster with that registry entry removed.
How about cleaning up your desktop of everything but folders. I read somewhere that Windows keeps files on the desktop in RAM in case you need them. If you just downloaded a big program to your desktop and it stays there it will clog up you RAM.
Also if you install a lot of programs that add choices to your Context memory, it takes Windows longer to rebuild the menus each time you right click. Get rid of those programs or using a context menu editor I would think would speed up your Windows experience.
This article is nothing more than click bait for there windows speed up guide. George Edward Purdy's post contains more useful information than this article. Quite the contrary, read this. It's possible for Windows to actually use up to 3.
If your graphics card uses shared memory like almost any onboard graphics, it will be less because part of it will be used by the graphics card. Please correct that in the article. Revolutions per minute abbreviated rpm, RPM is a measure of the frequency of a rotation.
It annotates the number of turns completed in one minute around a fixed axis. It is used as a measure of rotational speed of a mechanical component. I have tested that a couple of days ago.
I was using my new laptop without antivirus and it was amazing. Then I had to install the antivirus and I felt the slow-down. For example, now Autocad hangs very often, HD videos won't play as smooth as they should be, some programs like Word froze for some seconds So, I f you want your computer to work fast, you should disable your antivirus I believe that you should be safe as long as you know what you download from the internet and how secure are the pages you visit.
You're a damn fool. The recent malware distribution through Google ads should be evidence enough for anyone that "knowing what you download" doesn't provide any real safety. Malware can come from known and allegedly "safe" sites.
But go ahead, continue to surf the net without antivirus protection. We won't have to listen to your nonsense for too much longer, if you do. Anyone who disables their antivirus or doesn't use one is a damn fool.
I've seen a Windows Server get hacked in a matter of hours without antivirus and there was no budget where I worked for server-grade antivirus. Any day now your ISP will cut you off for helping to spread malware. The first thing I tell people to do with a new Windows pc is uninstall all the prepackaged bloatware or have a pro do it for you.
The second thing is to keep clicking 'deny' when installing new software you actually want until the final 'install' tab pops up. You'll end up with 10 toolbars on your browser and lord knows what else in your files if you don't.
Finally, not to be "that guy", but my pc with an AMD fx 2. So depending on need, other operating systems are an option too, especially for older systems. Why does Windows slow down?
That's what I thought, why recommend a guide that contradicts what you are recommending people do? Be careful about stating Windows 8 has its own security applications for the casual PC user who reads this article. There are those that bog down your system and others that have a small footprint and resource requirement.
I use BitDefender that provides good protection, small footprint, and small resource use. Thank you for pointing out the difference in RAM use on a bit system. Out of all of the myths, adding over 4 GB of RAM on a bit system is the one that is most believed by users in my experience.
I've seen so many articles about how MSE repeated failed antivirus tests. It's the last line of defense for people like the idiot commenter here who said antivirus doesn't do anything but slow the computer down, and he turns it off because he "web surfs safely.
If this article is about speed, not space, something like CCleaner isn't going to speed you up either. This is what I do for a living. I make slow Windows machines fast again.
Despite the assertion of this article, malware is the number one reason systems slow down. I routinely see systems that are crippled due to heavy infections of spyware and viruses. Rootkits are the worst offenders, of course, but even just a few unauthorized running apps in the background can slow a Windows machine to a crawl.
Anyone that tells you different is selling something. Typically I run at least 3 scans, and 2 immunization programs to eliminate spyware problems, and if I believe there is a virus or rootkit I have specialized tools just for those purposes.
Some other things I do to speed up a system. Sometimes this is "real" speed and sometimes it's perception of speed. Disable visual effects life window fade and zoom. A few seconds of effect are essentially wasted time.
Although it's designed to speed up searches by pre-indexing files, do you really search often enough to waste that many clock cycles in the background on indexing? It's a stupid feature. Disable it in Services. You can argue all day long about whether or not this really speeds things up, but I've been using this trick for years without fail on many systems, and it feels snappier on many system.
If you notice a problem you can always re-enable it. Repartition the hard drive and put the swap file on a dedicated swap partition. This also gets the swap file out of the way of other file write operations, preventing file corruption and fragmentation problems.
If you're going to defrag the hard drive, use Auslogics and move the system files to the front of the disk. If you can afford to upgrade, switch your main volume to an SSD. They've come down in cost, and this is one upgrade that will give you a real speed increase.
Windows isn't efficient with RAM, so you need as much as possible, and it's so cheap now compared to the old days. Update drivers, especially graphics drivers.
Look for system devices that don't have their own drivers. The default VGA driver is slow as crap. Make sure you have a real graphics driver installed. Disable or uninstall anything that runs on startup that isn't essential.
There are so many of these things. Even anti-spyware programs use these. It's annoying, and the more of these things you're running, the slower your system is. Winamp and Spotify and Nero and so many other programs have little components designed to run in the background or in the tray area.
Disable all that crap. You don't need it. It's drag factor on your system. Use either Autoruns or the Anvir Task Manager to check and see what's running. Malware is the number one cause of a slow-running computer for most neophytes.
The problem is that people search for programs like 'youtube downloaders' and most of them are infected with malware that installs MORE malware. And yes, I classify most of the software like 'registry cleaners', 'shopping assistants', 'search bars', etc as malware because of the way that they piggyback onto minimally functional software pretending to be the software that the user wants.
They don't need to actually steal data to be an impediment to a fully functioning system. Come to think of it; I think the stuff that George wrote here is better than this entire article. George - novice here - I found your comments to be invaluable.
Unfortunately, I don't know how to manually do most of what you recommend. Any guidance for people like me? George Edward Purdy; Could you please tell me how you "market" your business of speeding up computers? An in-home office has limits, traveling to individual's places to do the work, which can take a few hours, can be an inconvenience, having "workshops" can be difficult without being able to set pricing without knowing the number to show, and working at businesses for groups to bring their computers will almost always draw objection from any IT department.
Regarding point 3, it all depends on what is being done with the system. I have seen people follow this type of "tip" blindly on systems with 8 GB of RAM and then complain that their video editor is now running like a dog.
If no memory-intensive processing is done on the system, disabling the swap file is a viable option, but something like this needs to be thought through first for any potential ramifications. And for point 4 "This also gets the swap file out of the way of other file write operations, preventing file corruption and fragmentation problems.
I'm pretty familiar with Windows, so I already new most of this. What I really need help with is Android -- my two-year-old tablet running ICS has been crawling and crashing lately.
Any chance you would write a similar guide to Android? The problem is android in itself, and the fact that it's made in java. The performance of an OS made in C compared to that of an OS made in Java is huge, because Java has too many dependencies, it's too fragmented, and that's why we see an iPhone with a much worse CPU and RAM memory performing as well as if not better than the top android smartphones today.
I love my android, but that's how it is, if it was made in C, it would never lag like it does, and we'd all be living happily ever after with it, but we won't. Only thing I can suggest you is to use Clean Master to clean things like you do with cleaner, and boost your RAM from time to time, it really does make a difference, but you have to use it frequently as the way android works is apps relaunch themselves even if you kill their processes.
Not sure where you got your info Arben, Android is Linux at the core. You know, the same software that runs the best things in the world. Perhaps you are confusing the fact that applications that extend the functionality of Android are developed primarily in the Java programming language?
There are some application frameworks which include Java-compatible libraries but at its core it is still Linux kernel. While Google is your friend so is the wikipedia on Android. Perhaps some time reading would prevent you from confessing your ignorance out loud?
Ben, kind of everything. Apps take forever sometimes several minutes to load, often freeze or crash, sometimes when I didn't even know they were running. I will launch PlayerFM, it will take minutes to open, and crash when I try to play a podcast.
Or, I might randomly get a message the Amazon Kindle app has crashed, when I haven't opened it since restarting the tablet. Everything works eventually, if I'm patient enough, and I'm willing to restart the app if necessary.
I looked at Clean Master on the recommendations above, but I don't think I need a space manager or general task killer. I just installed WatchDog, so I'll see if that helps at all, but I'm open to suggestions.
Obviously you can't be all too happy about running on java vm coded apps, but it's changing, and, getting more and more optimised. The one tip you overlooked is using something like CCleaner to clear out your temp files.
I have seen folks regain literally gigabytes of space just by cleaning up temp files. CCleaner is good for cleaning temp files, but that has nothing to do with what the article is about - Speeding up your system!
I have to disagree with that Alan; temp files are indexed in Windows. The larger the index, the more your system must look through when it needs to access those temp files. While it's not always the best practice to clean them out, doing so can definitely give a performance boost when running applications.
CCleaner is related to what the article is about if cleaning out the temp files provides enough extra space for dynamic storage during program operation. The article states that lack thereof can cause system slowdown.
I've used CCleaner and other file cleaner programs to maintain some last gigs of hard drive space and thwart slowdown when i'm not able to immediately buy more drive space.
While I agree that the start-up configuration is one key area, I see on a daily basis as a call-out engineer 'slow-downs' caused by all of the above. Of course this depends on your description of a 'slow-down' I think of it as 'any symptom leading to a loss of expected productivity'.
Malware can cause pop-ups, search engine hijacks, and a raft of other 'slow-downs' while browsing, errors in Explorer and other embedded components serve to hinder.. What are these if not 'slow-downs'.
And no mention of fragmentation!? Thank you for being a voice of reason.
Speed ccleaner wiki once upon a time girls
How to Clear the Memory on Your Computer's Hard Drive. Having low memory on your hard drive can cause your computer to malfunction, and you won't have much space for. I remember one time back in the XP era I ran CCleaner once then stumbles upon this OP's question "Can someone explain why CCleaner has gotten.
24.01.2018 - May 23, at 7: It's shifting away from the "speed up and save space" era to more of a privacy tool. Similarly, I would recommend this especially to programmers.
Ccleaner windows 7 64 bit download - Clean app for... Email required Address never made public. Amazing that he got such a good cast for this rather tame product. Thanks for helping us achieve our mission of helping people learn how to do anything.
Version ccleaner wiki once upon a time torrent.
11.02.2018 - I am only thankful for this blog and in no position to complain. AlanS - Thanks for your profound comment on economics. Sometimes these cleaners tend to make a complete mess of the registry, which may cause other major problems that may make your computer completely inoperable.
Ccleaner gratuit pour windows 10 en francais - Pro... The iPad isn't as convenient as my 32" telly. I can see Silverlight start then a few seconds later, no connection. April 9, at 5:
Youtube downloader and ccleaner wiki once upon a time.
19.03.2018 - You don't need it. Under internet explorer check temporary internet files, cookies, and last download location. It doesn't really speed up the PC.
Ccleaner professional plus free download full vers... Each individual has their own optimal level of pressure and volume of fluid. Well, just forget it, I give a crap bout u and u give a crap bout me. As Sean pointed out, WOT is a great tool for the average user, but In today's Internet environment, even experienced users can fall prey to online scams, rogue software, phishing and other security threats.
Apr 25, · Tutorial: Tuning mods and Commodity Kinds You can get more information about ITUN resources at Simlogical: ITUN modding discussion An updated list of. Ccleaner is one of the best Five tips for using Ccleaner to degunk your system. Ccleaner will go so far as to remind you to back up the registry every time. An extremely hygienic man uses his urge in his professional life as a crime scene cleaner. Leonardo DiCaprio in Quentin Tarantino’s Once Upon a Time in 17%(12).
If you are on a Windows computer you can defragment your hard drive to put fragmented data back together and help your computer run more smoothly. Once open, click Defragment disk to begin.
This might take some time. Viruses can slow down your computer and take up precious space on your hard drive. Another way to clear memory on your hard drive is to remove viruses.
On windows you can use the Microsoft Security Essentials program to scan and clean your computer, or download a virus scanner application like McAfee. Upload documents to a cloud drive.
Using a cloud drive is another viable option to clear memory on your computer hard drive. Free up inactive memory to create more RAM. If it is too full, it can clog up your computer.
Another way to free up RAM is to limit the amount of programs your computer automatically opens upon startup. Use an external Hard Drive. RAM is sort of like short term memory while your Hard Drive is like long term memory.
By using an external hard drive you can free up both on your computer and reduce how hard your computer is using. Remove unused disk images. You can clear memory by ejecting disk images from applications or other files you have downloaded.
This is more for Macs than it is Windows. This also goes for any external hard drives you have plugged in. Clear up browser history and cache. It has long been known that these are insufficient due to the likes of resonance effects and non linear dialectric effects.
Whilst the NRPB do give a "hat tip" in the direction of resonance effects they do in effect ignore other known issues. The simple fact is neither politicians nor the industry want more exacting regulations for the usual reasons we have seen played out almost countless times before.
The result is no real research is carried out nor is funding made available for it, and the little that does happen usually gets published in very obscure places.
However as others have noted, what were once very rare cancers in the head and neck are now becoming more common since the use of mobile phones. Whilst we can not say if this is due to mobile phone use or just better diagnostics, I would recommend prudence.
Thus my usuall advice to peoole is "use hands free" as much as possible, and "where possible don't hold the phone". That is don't carry it around in your pocket up close to your body, and try to use it by putting it on a table etc when using hands free.
We might not like it --I certainly don't-- but Politics is part of the human condition at all levels. Likewise though few in the general poplulation appear to realise it these days Security is part of the human condition at all levels.
The reason is that "competition for resources" has and always will be part of the human condition at all levels. Hence the sarchastic "First amongst equals" saying.
Thus part of the problem is not "Politics" but "Relevant Politics" likewise it's also in part not "Discussion" but "Reasonable discussion". In recent news a person has been sent to jail for making what is probably just a crass comment, certainly a lot less objectionable than what some comedians have done in the name of humour.
We can learn another lesson from this which is "Venue and Audiance". That is the venue has to be appropriate and the audiance unlikely to be offended in some way. But also another element, in the case of the person sent to jail they were fairly reviled due to other actions they had taken.
Thus they had made themselves a target and had drawn significant ire from society upon themselves. Which gave others the excuse they needed to behave in the way they did by sending them to jail, which was most definatly "Dirty Politics" in play, but few if any will object because the person effected was reviled.
Thus some may view those who argued for the jailing as "heros" when at other times with other people they would have been regarded as at best loathsome. Thus though it should not mob rule was in effect invoked as in lynching parties of old.
Which makes politics also very context sensitive. Thus the problem of trying to define what is and is not acceptable is not just difficult it also suffers from variability due to contect, social perception and a number of other variables.
As I've indicated in the past there are reasons why I do not have my own blog, and politics is one of them. Thus I in no way envy the task Bruce and the Moderator have. I also from time to time post links I think might be of interest or a heads up for future threads, as I'm also aware of just how much effort it takes to find things of relavance, and also how easy it is to miss the first sign posts of something that may become big news.
All in all it seems very well thought out. Services like the one below, which create a 3D representation from a picture, won't work for the reasons already explained:. This article on why Open Access to scholarly journals and books has effectivrly failed, might be of interest,.
I was wrong, Planet B does not have a frozen core, but it will freeze sooner. Clive - I'd go a step further and say that Politics and Security always have been part and parcel of the human condition, to the point that both deeply affect our physiology and our consciousness.
I could hope that driving that point home was important enough to leave some minor stains on Bruce's living room carpet, and I'm happy to stay late and help clean up. I don't want to shy away from discussing torture and other violations of international law by the Deep State and other actors, but I'm fine with avoiding a focus on them and trying to get back to the business at hand of secure machines.
I don't seem to have tied diver area denial to lithotripsy, although immersion of someone's head was noted as a method for coupling high-intensity ultrasound to the brain and the Navy research on diver health effects also was noted.
I've been reserved in pointing out threat models, because I don't want to contribute to further violence. AlanS - Thanks for your profound comment on economics. I always believed in free markets, until I realized that there never were any.
I realized some time ago how little I know about consumer behavior after reading finely-detailed theories about preferences for goods, including Veblen goods. I haven't watched TV for a dozen years and only sparingly from the early 's until then.
Marx may have been correct about the opiate of the people in his time, but there are new ones now. I talked to one of the Deep State cogs yesterday, whose body language and facial expressions confirmed that everything, everywhere is recorded, even though he was constrained from saying anything.
FPGA enables a level and speed of compression to keep the cost of disk space in reach. I use biometrics here to include compressed formats for gait, which are unique. I have a blend of OCD mild, ADHD serious, and Asperger's mild, as well as a healthy dose of paranoia, so it is easy for me to obsess about writing long and tedious screeds.
I have been wrapped around the surveillance axle for a long time. I just don't want to drink a nice cup of tea alone". And even if apple could be trusted, which the past strongly suggests not to do: Keep in mind that face recognition is considered to be one of the current miracle pills against all things evil.
Diverse countries are starting FR in lots of public places and agency buildings or start to openly do what they did anyway but covertly. A billion or so high quality ready available face profiles will make many politicians think greedily and have their pens ready.
I've been known to talk about beauty and elegance in engineering and using it as an argument not just for engineering practice, but the likely "fitness for purpose" of the end product.
But as we know there is an awful lot of "out of sight out of mind" behaviour where those payed to do a job take short cuts that often fatally weaken the end product when stressed[1]. Frequently it is the customer that ends up hurt not just financially.
Some people end up saying the the situation "stinks" which is indirectly a refrence to the fact the product is rotten. Well It appears I'm not alone when I say "this code stinks" or more politly say it's "malodourus",.
And I personally look forward as do others when there are real regulations with teeth inplace for commercial code. Because such behaviour appears endemic and can be quite profitable, we end up with legislative regulations to prevent such behaviour.
Something that has yet to make it into the software business One of which is "voice inversion", which could be understood to a "trained ear", or Single Side Band type techniques. Which gave rise to Split Frequency Band Inversion, which although harder to break is still relatively easy.
Well Windytan who has an interesting blog has written up on it with some rather nice explanitary graphics,. Re "beauty and elegance in engineering" I fully agree and have mentioned it occasionally myself.
The truth comes up in the comments where she explains the reason for writing that post: Which leads me to a side note: Like the omnipresent nil null check based error handling. Besides some quirks like semicolons after ends or not explanation: You just don't know about it apparently, that doesn't mean it doesn't exist.
I don't see anyone having a responsibility to explain it to you, google it. How is this even a question? UHF can be directed relatively easily, and there is going to be interference patterns when you're shooting into a 3-D room layout obviously, you should hire a sound guy if you don't believe it's entirely reasonable to expect this.
That's the problem with having a lot of enemy nations around the world due to a hegemonist and antagonistic economic foreign policy, you're going to effectively piss off large swathes of the world and your attack surface area is huge at the same time.
There's no reason to suspect any particular group of these attacks among those so motivated, the technology certainly isn't brand new stuff. Its use in this way is possibly not even new, but we did not publicly know about this use until now.
To assume it was Cuban agents because it happened in a Cuban hotel is a bit naive in the world of spycraft obviously. Plenty of groups see Canada as connected to the US hip, and how the "Cuban Government" "feels" "publicly" about Canada for PR reasons really has no bearing on a potential motive either way.
Occam's razor cuts two ways - you are doubting a specific conclusion based on questions that you answer with your doubting assumptions that turn out to be false. As Trump would be right to note, jumping to conclusions without evidence in an ongoing investigation is usually a bad idea regardless of whether the guess turns out to be correct or not in the end.
Using the mask of questioning to doubt a specific conclusion is just good old bias. Clive - I stumbled into this today, because I sent it to Phil Zimmerman the day after posting it in a comment here in I think that it nails some important aspect of your recent comments on how one comes to be a good engineer:.
Intuition from experience is an essential feature. I am more of a scientist, but I was a passable engineer back in the day. There is more good content in the comment:. Rachel - I missed when you joined the discussion, but this comment and this link is on point for your desire to foster valuable skills:.
There have been a lot of studies showing reasonably low power EM at short distances can cause albumin to cross the blood-brain barrier, along with anything foreign the albumin may be carrying from the bloodstream - say like fine aluminum powder present in all of us or any other contaminant that binds somehow - and once there, it has no escape route.
Add to it new chemicals never found in nature until they became prevalent and in fact overwhelmingly prevalent in the last years, microplastics in tap water and bottled water alike, contaminated food chains with pesticides built-in to kill at unstudied rates and longevities, aerosolized metals from pollution sources, changing diets to mass-produced bleached bits of sterilized grain husks The very idea is a con.
Every merchant, every producer, every consumer has values and requisites and limits. Growth without a thought as to how or why is a boon in economics, it's the goal. We all know it as cancer, locally.
Economics is an idea and can't die. We have no such immunity from the reality of our self-poisoned world. Even if we don't even have the honesty to admit this is what we're doing, who still thinks it's noble to accelerate towards mass extinction for these economic paradigms?
Somewhere in a well-stocked bunker somewhere, anyone still think this is a good plan? In comparison, Tail's Tor browser recently yielded about 1 in Are there some good ways to get larger numbers in iOS devices 1 in a smaller number.
Javascript and cookie changes don't seem to matter much. Finally accessing the internet recently from an open wifi, portal capture, free wifi Tails was unable to synchronize the clock. With a non synchronized clock, I assume it might be easier to trace and individual Tor user around the world.
Is that a valid assumption? Not only is it not new, I've explained it on this blog a few times in the past, so older blog readers should be aware of it. The idea of generating very narrow beams form wider beams goes back atleast as far as WWII with the German radio direction control beams[1] such as Knickebein literally "crooked leg".
Which were a further development of the "Lorenz beam" blind landing system. Early work in Teddington UK in the Naval researche establishment next to the National Physics laboratory was using the idea of low end ultrasonic beams for making three dimensional ultrasound images --what we might now think of as holograms-- of boat hulls and other underwater objects and effects.
There was however an out break of what was thought to be dermatitis at the time by the technicians using it. This was turned into an early "non leathal" weapon for crowd control. However like other ideas it "disapeared behind classification".
It is known that like the Americans and "Paperclip" the Russian's in effect captuted and co-opted German Scientists who had experience with various beam type weapons Hitler had belief in advanced weapons and often took a personal interest, the idea of "Death Rays" to bring down aircraft was one.
Amongst other things it enabled the Russian's to get technically ahead on pre satellite missle detection systems such as the HF "Woodpecker" that has been mentiond here. Further it is known that the Russian's bombarded all diplomatic missions with various forms of energy beams from almost the begining to the end of the Cold War, much of the information about what was going on is still classified today.
It's been indicated that the assumption is that they were mainly "Active EmSec" attacks. However modern medical science is showing that the likes of electromagnetic fields at very low frequency does effect the functioning of the brain which has caused questions to be asked about medical imaging devices such as N MRI and Ultrasound.
It's also been shown that the Russian's were trying to develop various mind and conscience effecting technology given names like "Russian Sleep machine"[2] in the west to improve NREM sleep and were well ahead of what we now call "Transcutaneous Electrical Nerve Stimulation" TENS machines.
China also is known to use hypnosis and electrically stimulated acupuncture for loss of sensation for anesthetic free surgury as well as neurotoxins from bacteria such as Tetrodotoxin TTX that can be found in a number of sea creatures such as the fugu and lion fishes and varios octopi and crustaceans, one of which is said to be part of the "Haitian zombie drug".
Also sleep depravation studies whilst showing forms of hallucination along with other strange behavious from hours it fairly quickly reaches the point where the person either passes out compleatly or has micro NREM sleep.
The ones that get built for widespread, publicly 'acceptable' deployment and use are certainly not the only ones that get built. What is interesting here is not necessarily high-technology state of the art weapons being demonstrated, though it may be that too, but in my view the very selective targeting and discrete use that has so far publicly been unattributed to any actor - in fact obscured to the point that we don't even publicly know what TYPE of technology is being used to attack people.
So the finger points nowhere, in public at least. Cuba denied all culpability and no other nation is yet at all implicated. If it's going to be kept secret that we know who did it for reciprocity sake, why publicly admit the story is real at all?
If not known, that shows exactly how vulnerable diplomatic staff is abroad in 3rd party nations. One could note the reduced funding level for diplomatic state department programs we've seen lately. One could also notice that the US in particular and Canada by extension are in the middle of a serious diplomatic row with Russia and both are trying to apply pressure to pressure points in non-war ways.
Getting caught would be a major incident in a direct attack on diplomatic staff, the UN might even consider kicking them out over that. Putin would have to be at that level of will to do this, if it were his order.
On topic albeit technically off theme and illustriously underwhelming: It appears to have disappeared of theMSNBC website however, you can find the links in other articles,. In decades past Ham and CB operators could use illegal boosters to increase radiated power.
The FCC drives around in vans to pinpoint the culprits. Recently the FCC did not ban open-souce wireless routers. However manufactures removed, isolated and harden parameters relating to boosting or changing authorized radiated power.
However up until now, there is hardly any need to boost cell phone radiated power. It just has to reach the nearest tower. However malicious actors may be able to reprogram then command and control to damage owners in many hard to detect or little understood ways.
Smart-phone manufacture all have binding terms-of-service clauses of the possible dangers of this radiation. They are probably only liable for grossly negligent designs. Use the speaker phone. Don't take the phone to bed!
In any hostile location only use a dumb burner phone and land lines. This reduces precise phone number targeting. Tempest Rooms in Reverse Of course engineers will instrument areas of importance with single cycle triggered spectrum analyzers.
At sea the crews below deck are probably safe if their phones are secured, but NOT for those navigating. Hearing tests are recommended at least annually. I think this should be on top news everywhere.
It finally shows that IME is indeed bad for privacy and dangerous no matter what Intel says. And the possibility of being able to disable it means there's hope for the end user. I just stumbled into this, and thought you might enjoy seeing it if you haven't already: It's an octopus end table.
They don't seem to have squid end tables, but at least it's a fellows Cephalopod. I think that it might be due to the fact you don't see photos or pictures of squid folding their legs back above their head like that, where as you do fairly frequently with octopi.
The headline reads like "all your device are belong to us" and the first paragraph seems to confirm that by implying that any BlueTooth device can be hacked using this exploit.
Eventually, however, the third to last paragraph admits that Windows and iOS devices aren't vulnerable to this exploit at all and that Google is rolling out a patch the same day the article was published.
That was my conclusion as well. When I read it, I expected to see some major news, but However after reading it I was left with the feeling that the article had been cobbled together from this blog and our hosts postings Got your fish tank right here, pal!
Take, for example, Roomba, the adorable robotic vacuum cleaner. Ummm… Got your Roomba right here, bud! More than 70 percent of smartphone apps are reporting personal data to third-party tracking companies like Google Analytics, the Facebook Graph API or Crashlytics.
Got your ownership and control right here, dawg! We can do the same for all points mentioned in the article, but I am not feeling too well at the moment[1]. They only thing missing is some limerics, jokes, secret messages and C-v-P references.
Supposed to be a baked potato, but on the grill. At dinner time I looked in the fridge for the sour cream to put on it. Expiration date was three months ago. I said It's already sour, it can't get any worse, so I gobbled it down -- big mistake!
Thus, I am going to bed at an unusually early time. If you need a lift in your Monday Morning or any other time this week reading it might give life a little more perspective if not a smile or three,.
The proper process to resolve this mystery is to zoom in on the suspects most likely to benefit from the fear and harm resulting from the attacks. What changes have occurred in the usual suspects determined to kill the improvement of relationship between US and Cuba?
Are the attacks present on any Cuban government personnel and politicians. Has any American enemies of the usual suspects suffered from the attacks? But as far as tatty recipes roast potatoes in either duck or goose fat are supposed to have the best taste Almost feeling better now.
My hair can't turn green 'cause I have a good spleen ;. An amber alert woke me up! Colorado car license plate xxxx What am I supposed to do? Run out and look for it at 2: Do you get these stupid alerts in the U.
Oh, the blessings of a cell phone! Back to counting ducks and geese! I have been imagining microwave bombardment as a possible means because of locality, and some of the reported symptoms As I recall, a specific health danger of exposure to high microwave flux is the formation of cataracts in the eyes, believed to be a consequence of tissue heating.
It would be interesting to find out the results of eye exams of the reported victims As to the oft-suspected link between mobile phones and cancer, I remain skeptical for a simple reason. In recent decades, the incidence of brain malignancies has been declining slightly as measured in epidemiological statistics.
If mobile phone EM radiation has more than a very minute ability to induce cancer, then with billions of people who have been using such phones frequently for a good number of years now, we might reasonably expect a rising trend in brain malignancies, even if the average latency is very long.
This expectation should be amplified by the history of early adopters who used pre-digital mobile phones, which operated at much higher RF power levels. The observed trend suggests that if there IS a phone-to-cancer link, then there must be some separate factor s decreasing other-cause brain malignancies sufficiently to overbalance the mobile phone effect.
Not impossible, of course, but I suggest very unlikely. Note that by focusing on brain malignancies, I am not addressing non-malignant brain tumors, or head tumors other than in brain tissue.
I haven't looked at statistics for those categories. Hi MarkH, mobile phones radiation is directly implicated in brain and other cancers. There are countless published studies. Also remember its a multi billion dollar industry in bed with government and regulators, exactly as big tobacco was.
Governments, Scientists, Institutions across the world are moving on all kinds of limitations on what thus far is a global experiment on human health unprecedented in history.
The offical advice is 'Childrens brains change after 20minutes exposure-fact'. A colleague of mine whom specialises in the adverse effects of pulsed microwave radiation said last time he checked there were roughly 10, published papers referencing its adverse effects.
They definitely conduct the signal into the brain - definitely have all radio signals off if listening to music and don't use headphones with calls. Sancho-P you get me now There are meditation apps, Headspace being a famous one, for use with headphones and ones phone.
Its doubly bad and I find it crazy there is no reference to the EMF risk Not only are folks getting zapped. All the research demonstrates the brain and nervous system is most vulnerable to pulsed microwaves when asleep.
If one does nothing else, unplug the router and switch off all sources of transmission at night. One interesting observation I came across. A researcher commented, while they were not negating the known dangers of tobacco smoking: They noted lung cancers were moderately low until the introduction of AM radio towers populated the US en masse in the 50's.
There was a immediate spike in lung cancer uniformly, a direct correalation as far as she could see. JG4 thanks, as ever. The off topic stuff health stuff relevant for you, an area of expertise I wish to communicate I will paste bin or similar and let you know; cos it doesnt need a reply.
Tell us, what is Planet B you refer to? Wael - Thanks for the logic puzzle. I've always thought that there is a boolean matrix approach to this type of word problem and the related word problems with scheduling.
No more than nine students can ride in each raft, but never less than six are in each raft. Bob and John always travel in the same raft. Suzy and Kim hate each others guts so always will be in different rafts.
And end with a hard question like, "Will Suzy and John be in the same raft? Thy God, Profits - you raise some topics that I have been wanting to explore in biochemical security. Topping the list are the economies of Japan 1st, Switzerland 2nd, Germany 3rd, and South Korea 4th.
The United States sits in 9th place, and Canada is further down at 33rd. I am amazed that the US media blithely talk about military solutions without mentioning the collateral damage that would devastate South Korea, a US-client state with a world-class economy.
OODA loops don't execute linearly, so are not well-matched to a von Neumann architecture when fast execution is a priority. I don't see how the US is going to keep up with China for very long.
I am a regular reader of this blog, and this is my first post. Those looking for that kind of thing may wish to check out Daniel Miessler's "Unsupervised Learning" blog, a weekly set of links mostly related to InfoSec and technology, that I've found really well curated.
That's just a taste; she says much more. She closes with this: Do not send them, do not click on them. Use Whatsapp, use Dropbox, use a cloud account or hand someone a USB if you must, but stop using email to execute programs on your computer.
Good thing I've always treated it as suspect to begin with I can't even begin to imagine how many desktops this got. I echo Gram with his call to Ben A. Posting his list of links some known and accessible place elsewhere would be welcomed by me.
It has long been known that these are insufficient due to the likes of resonance effects and non linear dialectric effects It's been know for decades that bacteria can be killed by certain audio frequencies applied electrically to their medium blood or even our skin.
Even viruses can be destroyed this way. So one can selectively target certain cell types without hurting others. The key point is that frequencies rise as we move up the evolutionary ladder. Bacteria and viruses have kill frequencies in the hundreds of Hz, but multi-celled organisms have higher kill frequencies.
In the GHz range, we're close to mammalian frequencies, i. Imagine a weapon that can kill all of your white blood cells. OK, I don't even want to think about it. There is a complex system of energy channels in all creatures.
Ancient healing techniques are based on this. ALL - pasteurized - dairy products 'go bad'. Anyway, cows milk is for designed for cows offspring, not human consumption.
The more we eff with Nature, the deeper our graves we dig. It may be due to as yet unexplained energy effects. Those symptoms as a set is what you have with high or low intracranial Cerebrospinal Fluid pressure.
It is impossible to tell high vs low as the symptoms are the same. The medication Diamox, that lowers pressure, is often given to determine high vs low. This is less than ideal.
We are two years into a four year study. Each individual has their own optimal level of pressure and volume of fluid. It does not take a lot to upset the balance as the body does not have a closed loop feedback system for this.
Research is already known to exist on Gene Bombs, to take a out a single race, say Caucasian, by non-Caucasian adversary. CCleaner had a 3 week period where its bit version not 64 bit tellingly was compromised by a particular trojan that basically runs ONLY on 32 bit windows logged in with admin accounts - and anything else won't do.
If you're in that boat you're without exception making yourself vulnerable to drive-by already, but let's forget that for now. To pretend the entire ccleaner application tree is "no good" or "suspect" or "shady" based on a sole breach one that occurred after it was bought by Avast, one might note as if the source or authorship itself were somehow responsible for malware, suspect, shady, etc After all breaches happen with major software packages, github major.
The fact that it was detected within 3 weeks, fixed, disclosed, replaced, and the trojan in question is relatively easy to remove Compared to Java, flash, microsoft, android, bluetooth, 3 weeks is pretty effing decent.
Experian had their holes open for way longer than that, and that's a massive operation. Linux has year old flaws that just recently got fixed, more outstanding. To say CCleaner is shadyware because of a breach is just not logical.
Now, if they had tried to cover it up? Like a certain orange elephant in the room? That would be a different story now wouldn't it. I am only thankful for this blog and in no position to complain. I assure you they are not as long as they once used to be.
I think Nick P was keeping a link to what he indicated was the longest, and if not Nick P I suspect Wael can point out a few prize examples: With respect, that is not my reading of what is known.
There are a number of studies that have reported a small or weak correlation between exposure or proxies for exposure and malignancies. The position statements of various organizations and agencies that have health effects of EM radiation in their purview, are generally to the effect that a causal link between cell phones and cancer is not at present disproven There is no physical explanation for how cell phone radiation could damage DNA, nor laboratory evidence that it does so.
At the power levels of modern mobile phones, the temperature increase in bodily tissues due to radio frequency heating is believed to be far too small to have any medical effect.
At present, there is no theoretical basis to explain how RF from mobile phones might cause cancer. When, over the period of about 25 years, a large population is massively exposed to a new carcinogen, the rate of associated cancers would be expected to rise significantly.
You came to the right place! One by Nick P, and the other by truly yours Thanks for the helpful comments on logic puzzles. I always struggled with those. Could interstellar ice provide the answer to birth of DNA?
I thought that Ken Alibek did a good job of describing those. I trust that the regulars caught the reason in Secret History of Silicon Valley for the sudden US interest in radio astronomy during the cold war.
Rachel - there is only one other quasi-habitable planet in the solar system, which is Mars. I have been calling in Planet B. I don't have any good ideas for exchanging contact information, but I am open to ideas.
I noticed today that tightmail, which probably was mentioned last year, makes some interesting claims about an internal system of disposable intermediate email addresses that defeat metadata analysis. Long-range communication barrier for near-zero-power devices shattered https: I must apologize for coming back to my suggestion to Ben A.
Pastebin page with interesting links. Again, sorry for my crude metric? I think that Nick P. Regarding the overall solution to the problem, I think alternatives are often better than forcing monopolies to their knees through regulation.
Perhaps there is room for both. Well, I'd be fine with the link posts I do falling under this rule so long as I could post at least one link to a Pastebin.
After all, I wasn't usually reposting HN or Slashdot with my Assurance News and the like where I dug through obscure sites basically nobody reported on to get a list of research to bring to blog audience.
It also wasn't regular enough for me to have an RSS feed or something. You link to was a good page and people should re-read it from time to time, and it has some real gems in it further down.
For instance a link I gave showing just how journalists could by poor OpSec do real harm,. With the attendant admission that I did not think I could sufficiently lock down our comms end point devices and computers against level three attackers well equipt state level.
MarkH thanks for response. How am I going to explain an apparent decrease in brain cancer synonymous with the rise of mobile phones? And I would also question the source of your information. I appreciate you acknowledging the research is ongoing - indeed it is, the largest uncontrolled experiment in history!
But you know what - I'm happy for you to believe whatever you need to. It's certainly more convenient to believe mobile phones are harmless. Heaps easier, Waaaaay easier.
Science is not my god. I'm not one of these folks that only believes or disbelieves " thats been disproven!!!! I prefer my experiences, first, for things that directly relate to me.
As do millions of other people. It can be overwhelming in fact. To be fair and in good faith I will endeavour to provide the research I refer to. I can't promise anything as unlike a normal person I have no computer and like everyone else here life is very conplicated.
But it would be very good if I can support my claims so I'll see what I can do. I did a little more than alude to it a few days ago, I mentioned I had designed surveillance devices that work on a the Spread Spectrum principle back in the last century on this blog three years ago It's not the first and almost certainly won't be the last time academia eventually catches up with this blogs comments.
As RobertT once noted engineers know a heck of a lot more about the application of technology than researchers do, especially when it comes to things to do with security. Engineers in general do not have the "Publish or die" employment issue, in fact most of their employeers tend to encorrage the "Publish and we will ruin you" mentality.
Thus engineers tend to be fairly taciturn on the likes of security as our host has found out in the past. June 11, at 2: May 14, at 7: May 6, at 2: May 5, at 1: May 5, at May 4, at 9: May 29, at 2: Eddie Vedder not says: July 2, at July 29, at 9: August 25, at 9: April 30, at 4: January 24, at 1: February 21, at May 4, at April 23, at 3: April 17, at 8: April 3, at 9: May 3, at March 31, at 6: March 14, at March 11, at 9: March 9, at March 6, at 9: February 24, at 9: February 18, at February 9, at 8: February 9, at 3: February 8, at 4: February 1, at January 29, at 4: January 24, at 7: January 23, at 9: January 22, at 4: January 17, at 2: January 12, at 4: January 10, at 4: January 6, at 1: December 27, at 5: December 10, at 4: December 25, at 2: January 2, at 4: February 28, at 5: November 24, at November 24, at 8: November 10, at November 9, at 2: November 9, at 1: November 7, at 5: November 3, at 5: November 1, at 9: October 31, at 1: October 30, at 7: October 28, at 3: October 23, at 4: October 23, at 5: October 16, at 3: October 7, at October 4, at October 3, at 9: September 27, at September 24, at 9: November 19, at 2: November 21, at 5: September 13, at 9: September 9, at 4: September 6, at 3: September 29, at 8: November 22, at 9: January 16, at 3: January 23, at 1: April 6, at September 1, at 1: August 30, at 9: August 25, at 6: August 25, at 2: August 20, at 6: August 20, at 2: August 15, at 8: August 12, at 5: August 10, at August 9, at 9: August 9, at 7: July 30, at 9: July 26, at 1: July 26, at 2: July 23, at 7: July 18, at July 18, at 2: July 17, at 7: July 14, at 1: July 14, at 4: July 11, at 6: July 9, at 5: July 9, at 3: August 19, at 5: July 5, at 9: July 4, at 4: July 3, at July 3, at 7: June 30, at 6: June 30, at June 29, at 2: June 28, at 9: June 27, at June 25, at 4: June 21, at 2: June 22, at 3: June 23, at 3: June 20, at June 17, at 6: June 16, at 7: June 13, at 2: June 12, at 7: June 12, at 6: June 14, at 1: June 12, at June 18, at 4: June 11, at June 11, at 4: June 13, at 7: June 10, at 6: July 8, at 4: June 10, at 4: June 9, at June 9, at 7: June 9, at 9: June 18, at 8: June 8, at 3: June 8, at 1: June 7, at 4: May 31, at 6: May 29, at 6: May 29, at 4: May 29, at 3: May 26, at 9: May 26, at May 31, at May 26, at 2: May 25, at 3: May 25, at 4: May 24, at 8: May 24, at 6: May 25, at 8: May 25, at 9: May 23, at 7: May 22, at 7: May 23, at May 22, at 2: May 20, at 2: May 21, at 9: May 19, at 5: May 19, at 2: May 18, at 1: May 18, at 3: May 17, at 8: May 15, at 2: May 13, at 2: May 13, at 1: May 12, at 6: May 12, at 3: May 11, at May 9, at 6: May 8, at 6: May 6, at 3: May 7, at 2: May 16, at May 5, at 9: May 5, at 2: May 4, at 8: May 21, at 6: June 20, at 4: May 3, at 2: May 1, at May 19, at 3: April 30, at 3: April 29, at 7: April 29, at 4: April 29, at 3: April 28, at April 28, at 5: April 30, at April 27, at 3: April 27, at 2: April 27, at 4: April 26, at April 26, at 5: April 26, at 2: April 26, at 1: April 24, at 9: April 24, at April 24, at 7: April 24, at 1: April 24, at 3: April 23, at 1: April 23, at 2: April 23, at 7: April 22, at 3: April 23, at 9: April 25, at 1: April 25, at 6: May 1, at 8: May 2, at 9: April 22, at 1: April 22, at April 22, at 2: April 22, at 4: April 21, at April 21, at 5: April 25, at May 7, at 7: April 21, at 9: April 21, at 2: April 20, at April 20, at 9: April 20, at 5: April 20, at 3: April 19, at April 20, at 8: April 19, at 6: April 19, at 7: April 20, at 2: May 3, at 1: April 19, at 2: April 19, at 3: April 29, at 5: June 21, at 6: April 19, at 9: April 19, at 1: May 5, at 4: May 5, at 7: April 18, at April 18, at 5: April 18, at 2: April 18, at 4: April 18, at 3: April 17, at 3: April 17, at 1: April 17, at April 17, at 6: April 17, at 4: April 16, at 8: April 16, at 4: April 16, at 3: April 16, at 5: April 16, at 1: April 16, at 7: April 16, at 9: April 16, at April 15, at 9: April 15, at April 15, at 7: April 15, at 5: April 15, at 6: April 15, at 4: April 15, at 3: April 14, at 6: April 15, at 1: April 14, at 4: April 14, at April 14, at 9: April 14, at 5: April 14, at 2: April 13, at April 13, at 7: April 13, at 2: April 13, at 4: April 13, at 9: April 12, at 7: April 12, at 5: April 12, at 3: April 13, at 3: April 13, at 8: April 13, at 5: April 18, at 6: April 20, at 4: April 12, at 1: April 12, at April 12, at 8: April 11, at 5: April 11, at 7:



















Coments:
No sir...